- June 26, 2024

Are you confident in the security of your APIs? APIs are widely accepted and voluminous; the number of attacks and breaches that arise from these APIs has surged as well. This was revealed in the latest Imperva report, “State of API Security,” where almost ninety-five percent of companies reported having faced at least one security breach on their APIs within a period spanning from 2023 to 2024. Protecting sensitive data is fundamental and demands safe transmission through secure interfaces.
This guide explores API security testing, providing tips and methods to protect your systems from potential risks. We are sure, you would gain valuable insights on how to improve your security posture and also preserve your sensitive data against violations. This guide will help you stay ahead of potential threats as it deals with some expert strategies to bolster user trust.
Table of Contents
What is API Security?
Application Programming Interfaces (APIs) are a set of protocols, tools, and definitions that help in the communication of software applications. They specify how software components interact, allowing developers to access functions or data from external systems or services. APIs integrate, automate, and collaborate with diverse applications, enhancing user experiences and enabling seamless information flow.
- API security involves protecting APIs from attacks.
- API security is crucial for web application security.
- Most modern web applications depend on APIs to operate.
- APIs can allow external users to interact with an application, raising the risk to the API service’s infrastructure.
What is API Security Testing?
API Security testing identifies potential vulnerabilities and ensures secure data exchange. It also checks that unauthorized entities cannot access the API and it will also ensure that the API will be free from malicious code. Because the rate of hacking and exploits that aim at exploiting software vulnerabilities to access personal data is increasing. API security testing has become an important part of software development.
Historically, security teams performed API security testing through penetration testing or manual scans. Now, teams are integrating these tests into the DevOps pipeline, catching security issues early in the development lifecycle.
Types of API Security Testing
The range of API security testing methods available is extensive. Some require manual intervention, such as API penetration testing, while others are automated. When detecting a potential vulnerability in an API, certain methods may be more suitable than others. Bearing this in mind, let’s explore several types of API security testing tools.
Static API Security Test
Static API security tests help to examine the source code of your application. The main intention of this examination is to identify potential vulnerabilities. These tests will scan the codebase for security anti-patterns and other issues that might lead to security vulnerabilities.
Static analysis tools are language-dependent. Thus, you may have to choose a tool that would be compatible with the programming language as that of your API. While static testing provides valuable insights into code vulnerabilities, it may not capture runtime-specific issues and requires periodic updates to stay effective.
Dynamic API Security Tests (DAST)
Dynamic API security tests involve actively testing your API endpoints to simulate real-world attacks. This method is effective in identifying vulnerabilities introduced by both open-source dependencies and custom code.
Unlike static analysis, dynamic testing assesses the running application, providing a real-time evaluation of security posture. It falls under the category of dynamic application security testing (DAST). This is very much crucial for APIs. Traditional DAST tools may not be suitable for APIs. Therefore it is essential to use tools that are specifically designed for security testing the APIs.
Software Composition Analysis (SCA)
Software Composition Analysis (SCA) tools are important in the area of API security. Because they consider the dependency tree of your applications in order to find out whether it has any well-known weaknesses or not, by comparing the dependencies to a list of vulnerabilities, they can tell you when your API uses a library or framework that is not secure.
SCA is particularly crucial in today’s API development landscape, where open-source components are prevalent. However, SCA tools have limitations: they may not determine if a vulnerability is exploitable within your API, and they primarily focus on open-source vulnerabilities, overlooking potential security flaws introduced by your development team.
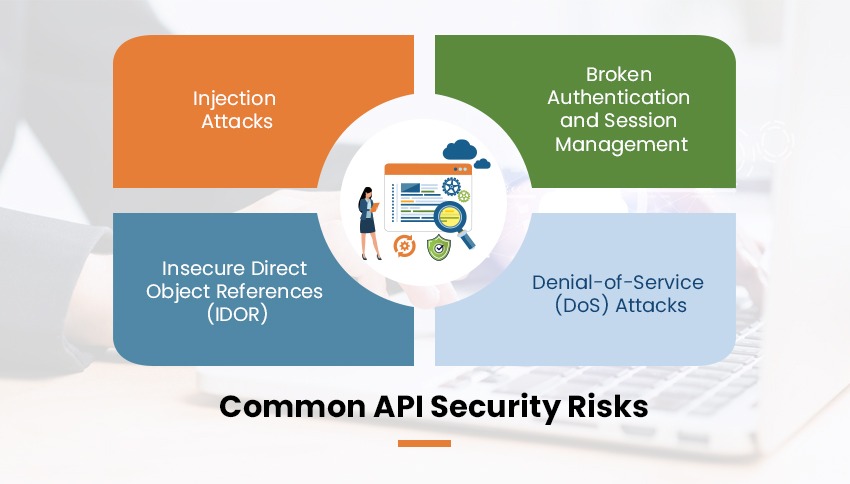
Common API Security Risks
Despite their benefits, APIs have several security risks,
Injection Attacks
Malicious code or commands can be inserted into API requests, leading to unauthorized data exposure, system compromises, or takeovers.
Broken Authentication and Session Management
Weak authentication, poor session handling, or insufficient access controls can allow attackers to impersonate users, hijack sessions, or access sensitive data.
Insecure Direct Object References (IDOR)
APIs with improper authorization can reveal internal references like database IDs or file paths and can open a window for hackers to retrieve unauthorized resources or information.
Denial-Of-Service (DoS) Attacks
Attackers are able to saturate the API with requests and, as a result, make it unresponsive or unavailable, disrupt services, and incur monetary loss.
How to Prepare Effective API Security Testing
Preparing for API security testing is crucial. We have to ensure the protection of sensitive data and also prevent potential breaches. The checklist to prepare for API testing is as follows.
Setting Up the Testing Environment
- Isolate the Testing Environment: Create a separate environment dedicated to API security testing to prevent impact on production systems.
- Replicate Production Configuration: Mimic the production environment setup, including server configuration and network architecture.
- Utilize Virtualization or Containerization: Use virtualization or containerization platforms for scalable and reproducible testing.
Identifying the Scope of Testing
- APIs and Endpoints: Define which APIs and endpoints will be tested, including internal, external-facing, and public APIs.
- Authentication and Authorization Mechanisms: Assess various authentication methods like API keys and tokens for thorough security evaluation.
- Data Validation and Input Handling: Analyze how APIs handle data validation and respond to different input formats to detect potential vulnerabilities.
- Error Handling and Exception Management: Evaluate API error handling to ensure sensitive information is not leaked in error messages.
Gathering Necessary Tools and Resources
- API Testing Tools: Select tools like OWASP ZAP or Burp Suite to support security testing. These tools also render a number of features like vulnerability scanning and API traffic interception.
- Security Testing Frameworks: Familiarize yourself with frameworks like OWASP API Security Top 10 to guide critical API security risks assessment.
- Documentation and Specifications: Obtain API documentation and specifications to understand expected behavior and security measures.
- Security Testing Checklist: Develop a comprehensive checklist covering authentication, authorization, input validation, error handling, and encryption for systematic testing.
API Security Testing – Steps to Follow
With the growing importance of robust API security, organizations are compelled to conduct deep testing so as to unearth vulnerabilities and lessen risks. Here are the steps that organizations should take for thorough API security testing.
Understand API Endpoints
- Define API Endpoints: Identify and categorize endpoints based on functionality and potential security risks.
- Identify Sensitive Endpoints: Determine endpoints handling sensitive data or critical operations.
- Map API Endpoints: Create a comprehensive map of endpoints for reference during testing.
Authentication and Authorization Testing
- Evaluate Authentication: Assess the strength of authentication mechanisms and user access.
- Examine Authorization Controls: Test authorization to prevent unauthorized actions.
- Test for Improper Access Controls: Identify misconfigurations allowing unauthorized access.
Input Validation and Data Integrity
- Analyze Input Validation: Evaluate how the API handles input to prevent common vulnerabilities.
- Ensure Data Integrity: Verify proper data validation and transmission between client and server.
- Test for Data Leakage: Identify risks of exposing sensitive data in responses or error messages.
Error Handling and Exception Management
- Assess Error Handling: Evaluate how the API handles errors and exceptions.
- Test for Information Disclosure: Ensure error messages do not expose sensitive information.
- Evaluate Exception Management: Assess how the API handles unexpected situations.
Rate-limiting and Throttling
- Understand Rate Limiting: Recognize its importance in preventing abuse and DoS attacks.
- Test for Bypassing Rate Limits: Verify if the API enforces rate limits consistently.
- Verify Effectiveness: Test the API under various load conditions to ensure proper functioning.
API Abuse and Security Testing Automation
- Explore Abuse Techniques: Identify and mitigate common API abuse scenarios.
- Implement Automated Testing: Utilize tools like OWASP ZAP or Burp Suite for automated testing.
- Leverage Tools: Use open-source frameworks for enhanced testing efficiency and coverage.
Benefits of API Security Testing
API security testing offers several benefits to organizations. It ensures the protection of sensitive data, maintains regulatory compliance, and safeguards the organization against potential breaches. Here are some key benefits,
Vulnerability Identification: API security testing helps identify vulnerabilities in API implementations. This helps in enhancing the security posture.
Data Protection: It safeguards sensitive data against unauthorized access. It also serves to protect data against breaches and privacy violations.
Compliance Assurance: API testing fosters adherence to regulatory requirements. GDPR, HIPAA, PCI DSS, etc., are some regulatory requirements.
Breach Prevention: Proactively prevents data breaches as it addresses security vulnerabilities.
Brand Reputation: Enhances brand reputation by demonstrating a commitment to data protection.
Risk Reduction: Minimizes security risks associated with API exposure to external networks.
Overall Security Improvement: API security testing strengthens overall security posture and resilience against cyber threats.
Best Practices for API Security Testing
Achieving robust security requires adhering to industry standards, staying informed about evolving threats, and implementing continuous monitoring and retesting practices:
Following Industry Standards and Guidelines
To guarantee there is strong security for API, organizations should follow the rules of their region, which is considered to be universal because of its importance, so as not to allow some cases where it will happen at all times without following them. This will help limit possibilities of breach due to gaps in this area that might provide hackers access into other parts where they may not only cause damage but also steal information if left unchecked.
Staying Informed About Evolving Threats and Security Practices
Keeping up with evolving threats is crucial for API security. Continuously, new attack vectors and techniques are introduced as the threat landscape evolves. This enables organizations to proactively identify and address vulnerabilities. This also helps them to stay informed about the latest threats. In this race to the top of security, active participation in security communities, attendance at conferences and leveraging threat intelligence sources serve as a front runner, helping the organizations remain ahead of attackers and implement timely security measures.
Implementing Continuous Monitoring and Retesting for Ongoing Security
Continuous monitoring and retesting are essential for maintaining ongoing security. Performing security testing once is not sufficient. APIs and their associated threats evolve over time. Continuous monitoring will help organizations to detect security incidents. This will also help them to respond to potential security incidents in real-time. It is also mandatory to perform regular retesting. This helps to identify new vulnerabilities that are being introduced by system updates from time to time or through the changes in the threat landscape. This iterative approach ensures that APIs remain secure and protected against emerging risks.
Enhancing API Security Through TestWheel
Ensuring the security of your APIs requires expertise and vigilance. To minimize the risk of serious breaches, choose professionals who are well-versed in the intricacies of API security testing. Such experts should be proficient in the latest advancements in the field and should have a thorough knowledge of the latest tools to be used for API security testing. Additionally, they should have good reasoning capacities, know the best way to go about it, and have prior experience in doing the same.
However, finding and retaining such experts can be challenging and costly. This is where TestWheel can help. TestWheel provides a cloud-based automated API testing tool that simplifies and enhances your API security testing process. You can effortlessly create and manage tests, automate API sequences, ensure comprehensive security with end-to-end testing, and use virtualization for scalable and reproducible environments.
Ready to enhance your API security? Contact TestWheel today and accelerate software quality through seamless and automated API testing.